Fake Skype analysis, es común por parte de los criminales imitar programas legítimos para tratar de infectar usuarios. Si consiguen crear una buena imitación de un software muy usado se podrá conseguir un impacto muy alto.
Fake Skype analysis, es común por parte de los criminales imitar programas legítimos para tratar de infectar usuarios. Si consiguen crear una buena imitación de un software muy usado se podrá conseguir un impacto muy alto.
En una lista de seguridad advertían de que habían subido a un repositorio de Sourceforge un instalador de Skype malicioso. Antes de que de retiraran el archivo me lo descargue para ver que es lo que era exactamente.
Tabla de Contenido
Fake Skype analysis y el archivo de Sourceforge
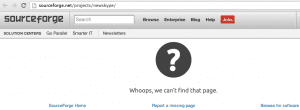
Por suerte el archivo ya ha sido removido del repositorio de Sourceforge.
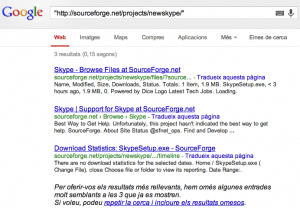
Si buscamos en Google, podemos ver que ya había sido cacheado por él.
El MD5 del binario es:
darkmac:pyew marc$ md5 ../../../Downloads/SkypeSetup.exe
MD5 (../../../Downloads/SkypeSetup.exe) = 4e6e4f03ae39c1273a7dd64c57ff2099
Antes de ejecutarlo en ningún entorno vamos a extraer algunos strings del binario.
Entre los strings encontramos cosas como:
Presuntamente podemos ver que se estaba compilando el archivo en la Unidad D:
Podemos ver mas strings interesantes
Estos strings pertenecerían al asistente de instalación de Skype.
Ahora usaremos una tool. que se llama pyew, para extraer mas información del binario.
Ejecutamos la herramienta.
Cuando ejecutemos la herramienta sobre el binario nos arrojará información sobre el archivo PE.
La cabecera MZ, indica que se trata de un ejecutable.
Tenemos un promtp desde el que podremos ejecutar ciertos comandos para sacar mas información útil.
Aunque los strings anteriores los hemos extraído del comando strings, con pyew podremos buscar strings en concreto en el binario.
Desde pyew, podremos buscar si el archivo está en Virus Total.
Alguien ya subió el archivo a Virus Total.
Análisis dinámico de la muestra SIN INTERNET
Aunque habitualmente subo el malware a mi sandbox con Cuckoo, esta vez he decidido usar una sandbox que me he montado. La sandbox es bien conocida por vosotros lectores, se trata de BSA (Buster sandbox analyzer).
Con esta sandbox puedo obtener rápidamente información interesante de lo que hace la muestra.
Para quien no lo sepa el ejecutar el malware en la sandbox de BSA, lo que hace realmente es ejecutar el sample en sandboxie.
BSA recoge los cambios que se han hecho y te los muestra en un report.
En este primer bloque, podemos ver los cambios que se han producido a nivel de sistema de archivos.
BSA también nos muestra los cambios del registro.
Se han cambiado múltiples claves del registro.
Aunque lo que mas me interesaba es lo que se muestra a continuación que es la parte de red, es decir, peticiones DNS, por ejemplo.
Aunque esta sección se trata de un análisis dinámico sin conexión a internet. He configurado con BSA, FakeNET. Este software nos ayudará en un análisis ya que si hay posibilidad de interactuar a nivel de red, FakeNET nos ayudará en eso.
En esta primera entrega hemos visto como los criminales usan sitios legítimos, como es Sourceforge para colgar archivos. En este caso han colgado una versión Fake Skype analysis, famoso programa para hacer multiconferencia, entre otras cosas.
Enlaces de interés:
[+]Pyew=> https://code.google.com/p/pyew/
[+]BSA=> https://bsa.isoftware.nl
[+]Malware analizado en Malwr=> https://malwr.com/analysis/N2E0ODA0OTYyZjcxNGQyMjkwZGU4YTgxYTQyOGY3ZWU/